|
|
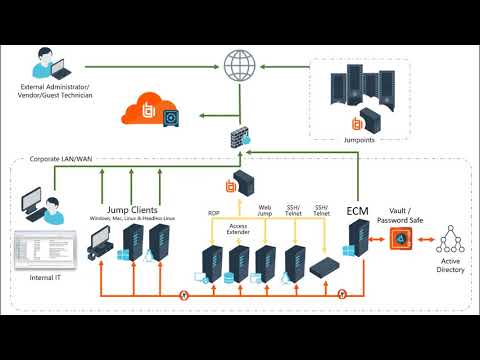
| Description | BeyondTrust PRA is an affluent remote access management software that empowers users to manage, secure, and audit internal and vendor remote privileged access with no VPN. Users can easily eliminate cybersecurity threat factors with this software. They also get to meet external and internal privileged access compliance requirements, with comprehensive session forensics and audit trails. Additionally, the platform comes equipped with prevention metrics like “privilege creep”, offering active protection of users' IT assets by enforcing the least privileges. Besides helping in vendor onboarding, BeyondTrust PRA helps to strengthen the IaaS accounts’ security by leveraging the existing security systems. Seamless integration with external password management solutions or BeyondTrust Password Safe helps users with their work in a seamless manner. The software lets users enhance the security of IaaS accounts by increasing the accountability related to root accounts besides enabling them to work across hybrid environments. Read more | BeyondTrust Password Safe is a risk management software built to reduce risks by filtering access to private and sensitive information, and account passwords. It enables the discovery, management, audit, and monitoring of all types of privileged accounts and SSH Keys. With Beyond Trust Password Safe, you can onboard accounts automatically and eliminate embedded credentials in code and script. You can simplify access requests, measure user behaviors and asset characteristics and set alerts to suspicious deviations. It enables secure logging and monitoring of sensitive credential activity and auditing by leveraging extensive analytics. You can additionally generate reports on benchmarks, suspicious behavior and compliance. Users get the option to automate onboarding and discovery to scan, identify and profile applications. Users can control files, codes, and scripts and embed keys to secure back doors of their system. They can additionally secure the use of SSH keys to improve security over Linux and UNIX systems. The platforms offer a free demo version to their users and you can request the pricing of their pro versions to access the premium features on their official website. Read more |
| Pricing Options |
|
|
| Organization Types Supported |
|
|
| Platforms Supported |
|
|
| Modes of Support |
|
|
| API Support |
|
|
| User Rating |
|
|
| Rating Distribution |
|
|
| Pros & Cons |
|
|
| Read All User Reviews | Read All User Reviews |
AI-Generated from the text of User Reviews
| Pricing Options |
|
|
|
Pricing Plans
Monthly Plans
Annual Plans
|
BeyondTrust PRA Custom |
BeyondTrust Password Safe Custom |
|
View Detailed Pricing
|
View Detailed Pricing
|
| Screenshots |

|
Not Available |
| Videos |
+ 2 More
|

|
| Company Details | Located in: Johns Creek, Georgia | Located in: Atlanta, Georgia |
| Contact Details |
+1-877-826-6427 |
+1-877-826-6427 |
| Social Media Handles |
|
Not available |
What are the key differences between BeyondTrust PRA and BeyondTrust Password Safe?
What are the alternatives to BeyondTrust PRA?
What are the alternatives to BeyondTrust Password Safe?
Which product is better for managing privileged access?
Which product is better for securing accounts and passwords?

Looking for the right SaaS
We can help you choose the best SaaS for your specific requirements. Our in-house experts will assist you with their hand-picked recommendations.

Want more customers?
Our experts will research about your product and list it on SaaSworthy for FREE.